WSO2 Identity Server supports for social login feature such as Google, Facebook, Azure and etc. Once you configure Google as federated authenticator, Identity Server will facilitate to authenticate with your Google credential. So it is not required to have those user details within identity server user store.
I'm using Identity Server 5.1.0 and travelocity sample web application for this demonstration. Also I'm testing this scenario with Google sub domain (i.e. wso2.com)
1. Download the identity server from [1].
2. You can configure travelocity sample web application by following the documentation [2]. If you have already deployed and configured service provider, you can ignore this step.
3. Register OAuth 2.0 Application in Google.
Here I'm configuring OAuth web application in Google by selecting OAuth Client ID. You can find more details form [3].
4. Create an OAuth 2.0 application in Google and generate the client id and secret from the application. Make sure to provide "Authorized redirect URI" as following,
https://{hostname}:{port}/commonauth
According to the default configuration of the identity Server, redirect URI should be,
https://localhost:9443/commonauth
5. Log into Identity server Management Console and add new Identity provider by providing Identity Provider Name (I'm providing "wso2.com" as my IDP name). Then configure the Google authenticator as shown below. Make sure to add your Redirect Uri as the Callback Url and Client id and Secret which is generated from above Google application [1].
6. Now navigate to your service provider configuration and expand the Local & Outbound Authentication Configuration section. Under that, please select "Advanced Configuration". Once you select this, you will be able to add multi-step authentication or multiple authenticators within one step. For the moment, we are selecting basic authenticator & configured Google authenticator within step one as shown below.
7. Now we have done the basic configuration, so check the scenario now. You will be getting a login screen as shown below,
8. Once you select Google authenticator(in my scenario its "wso2.com") , you will be redirect to Google login page. If you successfully authenticate, you will be redirecting to the web application with federated user details.
Hope this will helpful. Thanks you.
[1] http://wso2.com/products/identity-server/
[2] https://docs.wso2.com/display/IS510/Configuring+Single+Sign-On
[3] https://developers.google.com/identity/protocols/OpenIDConnect
Wednesday, October 12, 2016
Tuesday, January 5, 2016
Get a user profile for OAuth Token using JWT headers with WSO2 Identity Server
This blog will explain, how to retrieve user profile and view user's attributes using OAuth access token in WSO2 IS. I assume that reader is familiar with WSO2 identity server
and if you need more help you can follow the documentation at
http://docs.wso2.org/wiki/display/IS400/WSO2+Identity+Server+Documentation
1.
First we need to enable JWT token generation in Identity Server. Goto IS_Home/repository/conf/identity.xml and make
following attribute true.
<AuthorizationContextTokenGeneration>
<Enabled>true</Enabled>
<TokenGeneratorImplClass>org.wso2.carbon.identity.oauth2.authcontext.
JWTTokenGenerator</TokenGeneratorImplClass>
<ClaimsRetrieverImplClass>org.wso2.carbon.identity.oauth2.authcontext.
DefaultClaimsRetriever</ClaimsRetrieverImplClass>
<ConsumerDialectURI>http://wso2.org/claims</ConsumerDialectURI>
<SignatureAlgorithm>SHA256withRSA</SignatureAlgorithm>
<AuthorizationContextTTL>15</AuthorizationContextTTL>
</AuthorizationContextTokenGeneration>
2. Enable Admin services in Identity Server. Open
IS_HOME/repository/conf/carbon.xml
and set
HideAdminServiceWSDLs
property
to false.
<HideAdminServiceWSDLs>false</HideAdminServiceWSDLs>
3. Then start the WSO2 Identity server.
4. Create
a service provider with OAuth2. To
create a sample SP, Login to the Identity Server management console. Goto Main >
select Add under Service provider. Give
a name for a SP and select
register.
Goto
Inbound
Authentication Configuration > OAuth/OpenID
Connect Configuration and select Configure.
Put a call back url and select add.
5. Then we can get the Client key and Client secret as show below.
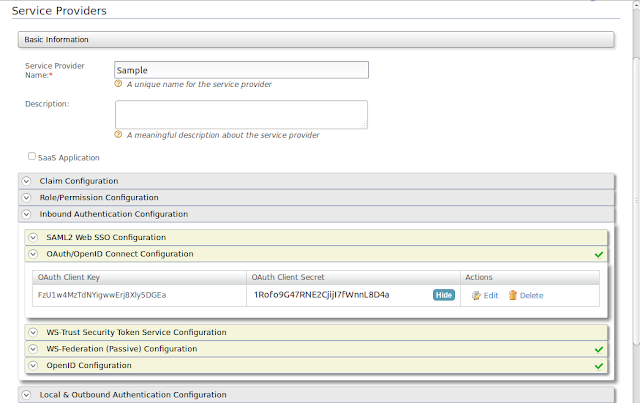
6. Get
the base64 encoded value for (client id:client secret) value. we
can use an online tool like http://www.base64encode.org/
7. Use
following CURL command to obtain the access token from the Identity
Server.
curl
-v -X POST -H "Authorization: Basic
RnpVMXc0TXpUZE5ZaWd3d0VyajhYbHk1REdFYToxUm9mbzlHNDdSTkUyQ2ppakk3Zldubkw4RDRh"
-H "Content-Type:
application/x-www-form-urlencoded;charset=UTF-8" -k -d
"grant_type=password&username=admin&password=admin"
https://localhost:9443/oauth2/token
8. Create
a SOAP web service project in soapUI using the following WSDL.
9. Then
send the request and get the authorization
context token which is encoded in base64 and delimited with "." character as
shown below.
10. The
Middle part will contain the user profile value and we can get it
decoded using http://www.base64decode.org/
<ax2337:authorizationContextToken
xsi:type="ax2337:OAuth2TokenValidationResponseDTO_AuthorizationContextTok
en">
<ax2337:tokenString>eyJ0eXAiOiJKV1QiLCJhbGciOiJTSEEyNTZ3aXRoUlNBIiwie
DV0IjoiTm1KbU9HVXhNelpsWWpNMlpEUmhOVFpsWVRBMVl6ZGhaVFJpT1dFM
E5XSTJNMkptT1RjMVpBIn0.eyJpc3MiOiJodHRwOi8vd3NvMi5vcmcvZ2F0ZXdheS
IsImV4cCI6MTQ1MTk3ODM2OTAzNiwiaHR0cDovL3dzbzIub3JnL2dhdGV3YXkvc
3Vic2NyaWJlciI6ImFkbWluIiwiaHR0cDovL3dzbzIub3JnL2dhdGV3YXkvYXBwbGlj
YXRpb25uYW1lIjoiU2FtcGxlIiwiaHR0cDovL3dzbzIub3JnL2dhdGV3YXkvZW5kdXN
lciI6ImFkbWluQGNhcmJvbi5zdXBlciIsICJodHRwOi8vd3NvMi5vcmcvY2xhaW1zL2
NvdW50cnkiOiJTcmlsYW5rYSIsICJodHRwOi8vd3NvMi5vcmcvY2xhaW1zL2VtYWls
YWRkcmVzcyI6ImFkbWluQHdzbzIuY29tIiwgImh0dHA6Ly93c28yLm9yZy9jbGFpb
XMvZnVsbG5hbWUiOiJhZG1pbiIsICJodHRwOi8vd3NvMi5vcmcvY2xhaW1zL2dpdm
VubmFtZSI6ImFkbWluIiwgImh0dHA6Ly93c28yLm9yZy9jbGFpbXMvaW0iOiIxcWF
6MndzeCIsICJodHRwOi8vd3NvMi5vcmcvY2xhaW1zL2xhc3RuYW1lIjoiYWRtaW4iL
CAiaHR0cDovL3dzbzIub3JnL2NsYWltcy9tb2JpbGUiOiIwNzc3Nzc4ODg4IiwgImh0
dHA6Ly93c28yLm9yZy9jbGFpbXMvb3JnYW5pemF0aW9uIjoiV1NPMiIsICJodHRw
Oi8vd3NvMi5vcmcvY2xhaW1zL3JvbGUiOiJhZG1pbixJbnRlcm5hbC9TYW1wbGUsS
W50ZXJuYWwvVHJhdmVsb2NpdHksSW50ZXJuYWwvZXZlcnlvbmUiLCAiaHR0cDo
vL3dzbzIub3JnL2NsYWltcy9zdHJlZXRhZGRyZXNzIjoiS29scGl0eSIsICJodHRwOi8v
d3NvMi5vcmcvY2xhaW1zL3RlbGVwaG9uZSI6IjA3MTIzNDU2NzgiLCAiaHR0cDov
L3dzbzIub3JnL2NsYWltcy91cmwiOiIyd3MxcWEifQ.jKYijQhFrWZRq9ddpxQ2dTGYj
VpCwOd8BOIpItW7v1pg-rbMdDGa14KcrWddL0nKUn1Wl3chUQsqtxaippUAPiSO0N7qqLbG1Qoe48COsAW
tFa_T7QBlzilwAffC3XAgdnqH20FcxK1_K3ttrvyfGR-Lhl7oyQsv8UcGsOSI6x0</ax2337:tokenString>
<ax2337:tokenType>JWT</ax2337:tokenType>
</ax2337:authorizationContextToken>
Hope this will helpful. Thank you.
Subscribe to:
Comments (Atom)









